Governance: Policy GV.PO: Policy
Organizational cybersecurity policy is established and communicated
Establishment and communication of the organizational cybersecurity policies, procedures, and processes defines the organization’s approach to management of cybersecurity.
Organizational cybersecurity policy is established and communicated: Defined
The basic idea of a policy is to keep multiple teams on the same page over the course of time with respect to an organization’s key ideas and values. Bad policy can be hard to see when you’re in an environment where it isn’t emphasized. So, if somebody in the organization has an agenda that is meant to obscure accountability (or perhaps one of a thousand other issues) via vague or ineffective policy, it might go right over your head without you even noticing. After all, everybody asks if you’re following policy, not whether a policy is a good idea or not, as people can get themselves fired for that kind of independent thinking.
Unfortunately, this kind of thing manifests very often in the InfoSec realm more often than in other areas. So NIST told everybody to check their policies and make sure that “cybersecurity” or its synonyms were included somewhere. In fact, it even called out the fact that cybersecurity policy isn’t allowed to be a “secret squirrel” policy. You have to actually communicate it for it to be effective. How novel! And a sad commentary too.
We’d like to add a few more steps, because adherence to vague policy is a defense that is used way too often. Observe the policy to make sure that not only is it established and communicated, but that it is also reviewed, approved, and published, to appropriate parties. The policy should outline the information security strategy, or the management’s intent with regard to cybersecurity. It should include principles or key statements regarding security which can be shared with stakeholders.
Key factors for consideration when developing the information security policy:
- Business mission and strategy
,
- Relevant regulations, legislation, and contractual requirements
,and
- The organization’s specific threat landscape.
Established
Develop a common and comprehensive cybersecurity policy, a set of standards, and a control framework. The CISO is accountable/responsible and consults with other technology leaders. Inputs for establishing the policy and control framework include strategic and tactical IT and cybersecurity plans, projects, and service portfolios. Other organizational assets will need to be included in the process, for example: risk management guidelines and legal and regulatory requirements.
If these seem like a lot of items—they are! You won’t be able to build everything up in one swoop. So make sure that a framework for policy, standards, and procedures is developed and that it includes a repeatable approach for defining scope, responsibilities, requirements, and consequences for non-compliance.
Reviewed
The policy, standards, and procedures should be reviewed at regular intervals as defined by your organization to ensure that the documents remain acceptable and relevant to the business needs. A common regulatory requirement is to review at least once annually. Review should also aim to incorporate continuous improvement of the documents in alignment with changes to strategy, processes, technology, and the threat landscape.
Approved
The appropriate level of leadership has to actually sign off on the policy document. Very often there will be interaction with the board of directors here. A leader’s approval of a policy isn’t merely ceremonial. HR requirements often include clauses that require an employee to comply with corporate policies, so lack of adherence can impose employment consequences on those who have approved a policy.
Accountability must also accompany approval. It gives policy violations a place to accrue in the organization. So if the VP of IT approves an information security policy, they must also act when they learn of violations.
Approval must also be given by someone at an appropriate level in the organization. Policies require authority in order to be implement. Generally, enterprise-level executives must approve policy, rather than divisional or functional-level executives.
Published
Cybersecurity policies should be accessible by everyone in the company. In the rollout employees should be informed of when to expect subsequent compliance checks. It is important to get buy-in from senior management when publishing the cybersecurity policy, standards, and procedures. This will support implementation and adherence. Monitoring, self-assessment, and compliance checking are pervasive within the organization, and technology is used as an enabler of the assessment and awareness process.
Communicated
Define and maintain a communications plan to communicate the cybersecurity policy. Various communication channels can be used including email, intranet, posters and training sessions. Communication should be confirmed through either attendance at a training session or acknowledgement of the documentation.
ID.GV-1: In the news
Organizational policy (and especially cybersecurity policy!) is, by its very nature, sensitive for leaders. In a way, the rules in a policy compress all an organization’s disparate activities and interests into one document. It can become something of a blunt instrument because a policy that is too prescriptive can be a burden. But policy that is too lenient might provide no value at all.
No organization is as large and diverse as the United States Department of Defense, which has seen more than its share of security incidents. Exacerbating the problem areis its hyper-broad mission and gigantic footprint, which make it challenging to get everything on the same level. Here’s a discussion of the new Cybersecurity Maturity Model Certification, that is causing heartburn amongst some Federal contractors.
My organizational cybersecurity policy: Failed…what am I going to see?
Hopefully you’ve found out that your organizational cybersecurity policy has failed because you can’t find it—or something. Because it could be worse, lfor example an auditor might ’have dug up something that was last approved in 2017, which isn’t a great conversation. In any case, look for existence, communication, and compliance.
404 cybersecurity policy not found.
Management has not established a cybersecurity control environment and has not recognized the need for a set of policies, standards, procedures, or compliance processes. The organization reactively responds to information security requirements and develops documentation on an ad hoc basis with inconsistent approaches.
Secret squirrel cybersecurity policies prevent accountability.
Employees are less likely to be aware of the cybersecurity risks and the steps they can take to mitigate those risks when the cybersecurity policy and standards are not communicated. Lack of awareness can lead to non-compliance with requirements. When employees have not attended training sessions or participated in acknowledgement campaigns for the policy and standards there is a high likelihood that they are not aware of their responsibilities related to cybersecurity.
Compliance is for the birds.
Never forget that policy is a prominent part of our defense against breaches, malware infections, social engineering attacks, and compliance violations. If your organization doesn’t have the time or interest to invest in compliance —that is checking for conformance to your defined requirements (which should be embodied in your cybersecurity policy, )—then you haven’t fully implemented the policy framework. Security requirements are selected to protect the organization from data breaches and, other security incidents, and to meet legal and regulatory requirements, as mentioned with regards to the negative implications from a lack of communication of policy.
My organizational cybersecurity policy: Is stellar; what does it look like?
The number one trait of a fantastic cybersecurity policy is that it is obvious and provides clarity on how things should operate. It should allow you to see the top-level requirements, and provide harmony between groups.
You can trace a cybersecurity policy all the way down to control activities —and back again.
Cybersecurity policy outlines standards which inform the design of controls activities. For example, customers demand that suppliers adhere to a relevant security framework, like NIST 800-53. That constitutes a standard, i.e. “For product xyz, we maintain controls consistent with industry-recognized security frameworks.” Then you might organize your controls consistent with NIST-800-53, which provides a structure for security and privacy control families:
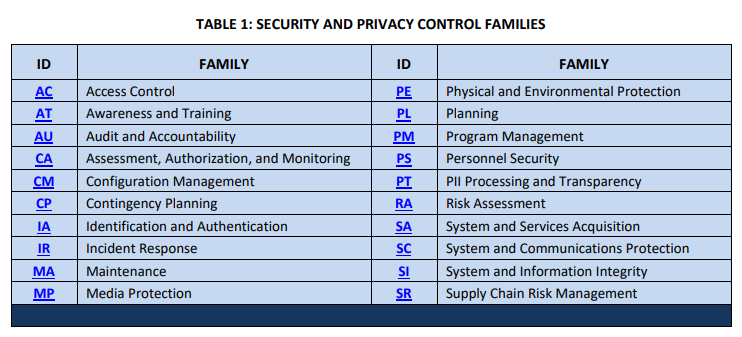
TABLE 1: SECURITY AND PRIVACY CONTROL FAMILIES ID FAMILY ID FAMILY AC Access.
Everybody has the same cybersecurity responsibilities.
The key thing to remember is that in most instances, if a bad actor gets a foothold in one part of the organization, they’ll likely be able to access everything in time. As if that weren’t bad enough, it is basically impossible to manage security if every group that plays a part does its own thing. There must be an organized and competent response to security requirements.
According to COBIT, the highest level of maturity for policies, plans, and procedures has a governance approach where “processes, policies, and procedures are standardized and integrated to enable end-to-end management and improvement.” Governance components include roles and responsibilities, repeatable processes, policies and procedures, skills and competencies, and assessments for continuous improvement.
There is no mystery in what the InfoSec department does (or doesn’t) do.
It can be easy to miss the handoff between one group and another. InfoSec and IT are notorious for finger-pointing in the aftermath of an incident. Most of this can be avoided by making sure that policy establishes responsible parties and facilitates accountability devices like SLAs or escalation paths. The International Standards Organization states this concisely in ISO-27001, “[T]he policy scope should be defined in terms of characteristics of the organization, location, assets, and technology. Any exclusions from the scope should also be defined and justified.”
Remediating or iImplementing organizational cybersecurity policy.
Cybersecurity policy is foundational to nearly every other cybersecurity activity. The key to remediating and implementing is to spend your time and effort where: (a) it supports your organizations mission, (2) it is cost effective and (3) it leverages everybody’s talents.
You are a special snowflake.
Organizations need to assess their own risks and vulnerabilities in order to develop a cybersecurity program that addresses their specific needs. While best practices and existing control frameworks provide a great starting point, it is not recommended that organizations use these “out of the box”, rather they should implement best practice in a way that makes sense for the specific organization’s culture, structure, cybersecurity posture, resources, and threat landscape.
You can’t have your cake and eat it too.
In most cases it is not possible to implement all best practices and known controls due to costs, priorities, and user experience considerations. Therefore organizations will need to develop a road map for implementation of missing process practices and controls that are necessary for the organization’s long term success. Metrics and dashboards can be used to support accountability and transparency in the implementation and maintenance of the cybersecurity policy and standards.
Everybody has a role to play and nobody plays all roles.
Security awareness that is specific to the roles and responsibilities of employees can help employees to be aware of their responsibilities and best practices most relevant to their work. Some groups to consider:
- Executives
–covering cybersecurity risks, governance, and compliance. - Developers
–covering secure coding practices, security testing, security architecture, and vulnerability management. - IT professionals
–covering security controls, incident response, and data protection. - General employees
–
Role-based training enables the organization to provide targeted and effective training for key groups of employees.
Cybersecurity policy: Other sources of authority.
Security and Privacy Controls for Information Systems and Organizations. NIST SP 800-53 Rev. 5. Security and Privacy Controls for Information Systems and Organizations (nist.gov)
Information security, cybersecurity and privacy protection: Information security management systems – —Requirements. ISO/IEC 27001:2022. ISO – ISO/IEC 27001:2022 – Information security, cybersecurity and privacy protection — Information security management systems — Requirements
A Business Framework for Governance and Management of Enterprise IT. COBIT 5. Store – COBIT 5 | Digital | English – ISACA Portal
Chatting Aabout Organizational Cybersecurity Policy.
Jamie talks to xyz: [Link1]
Resources for the journey.
Developing Cybersecurity Programs and Policies by Santos [Link]
“Essential Functions of a Cybersecurity Program” by Akridge via ISACA

Comments are closed